Online, Accelerated Post-Bachelors
Admission Deadline
Complete our Request Information form to be updated on upcoming enrollment information.
Request Additional Information
The Post-Bachelor’s Accelerated Cybersecurity Track utilizes an innovative online delivery modality – allowing flexibility for adult learners who have already earned a bachelor’s degree from an accredited institution of higher education. All courses are delivered online with an appropriate balance of synchronous and asynchronous elements.
Assumption University is an ideal place to learn – offering small cohort sizes and competitive pricing. Graduates will be prepared for rewarding careers in as few as 14 months.
The mission of the Cybersecurity degree program is to educate the next generation of cybersecurity professionals and leaders who are armed with the necessary knowledge and technical ability to prevent, detect, respond, and recover from cybersecurity attacks. Graduates recognize their responsibility to perform their jobs ethically and with integrity, thereby helping to secure, develop, and sustain the cyberspace ecosystem.
The curriculum is recognized by the National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA) who sponsor the Centers of Academic Excellence in Cyber Defense (CAE-CD) program and is targeted at educating the next generation of leaders and architects in cybersecurity, who possess technological expertise and practical training to help secure, develop, and sustain the cyberspace ecosystem.
Assumption University has been designated as a National Center of Academic Excellence in Cyber Defense. Read about it here.
Susan M. Cahill
Raymond T. Albert, Ph.D.
Learn more about the Post-Bachelor's Accelerated Cybersecurity Track
-
The Post-Bachelor’s Accelerated Cybersecurity Track utilizes an innovative online delivery modality – allowing flexibility for adult learners who have already earned a bachelor’s degree from an accredited institution of higher education. All courses are delivered online with an appropriate balance of synchronous and asynchronous elements.
-

-
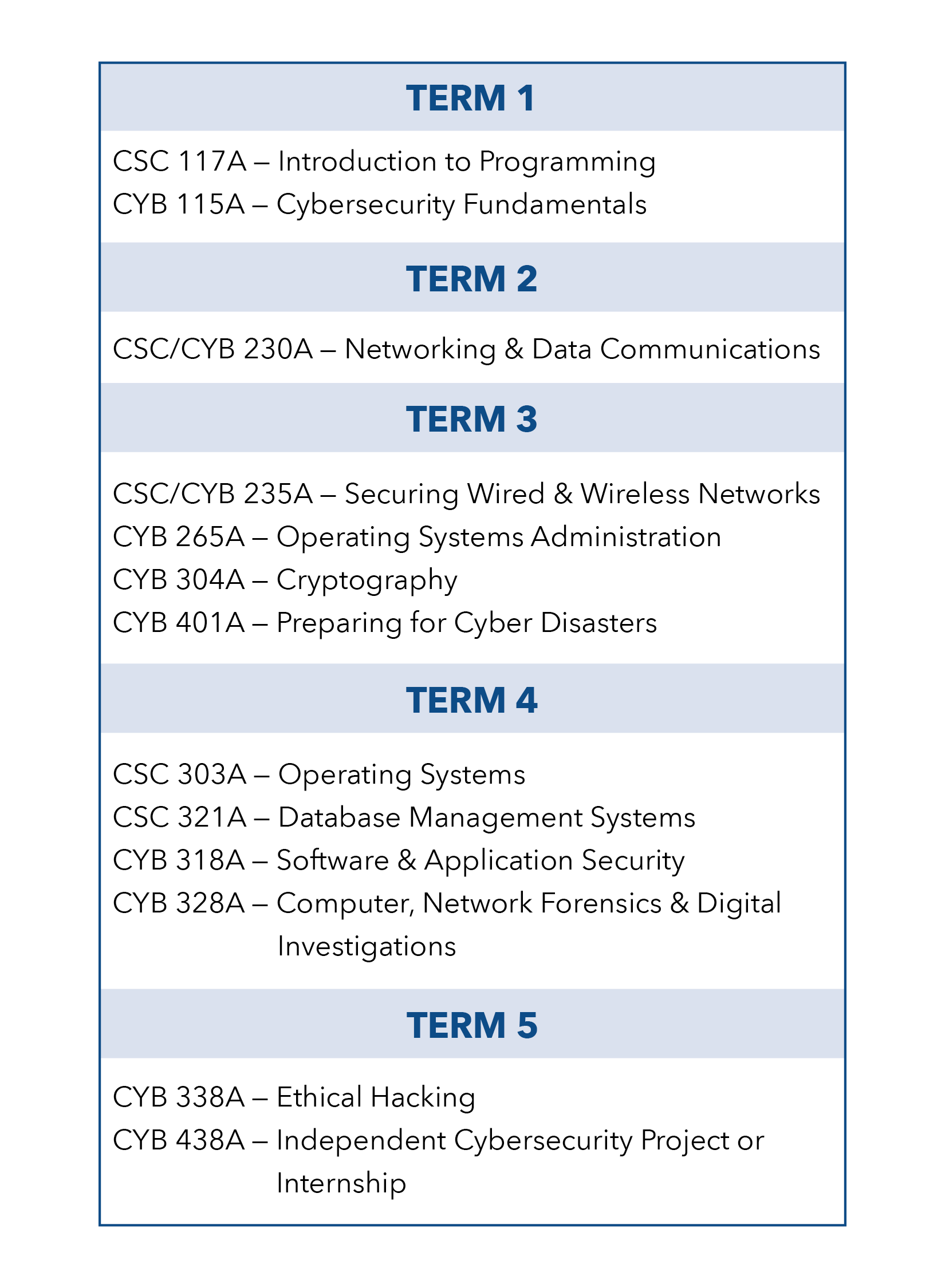
CSC 117A INTRODUCTION TO PROGRAMMING
This course is an introduction to the field of computer science and structured programming in C++. Topics include basic computer architecture, the algorithmic approach to problem solving, various number systems, and logic. The programming language constructs introduced include types of variables, arithmetic operations, input/output, decision statements, loops, and functions.CSC 303A OPERATING SYSTEMS
This course introduces operating system design emphasizing process management for multiuser and networked systems. Topics covered include: process scheduling, interprocess communication, race conditions and solutions, memory, device and file management.CSC 321A DATABASE MANAGEMENT SYSTEMS
This course deals with both the operational and decision support environment of database systems. Topics include indexing, randomization, physical blocking, and relational and hierarchical structures. Previous experience at the level of CSC 175 or equivalent is recommended.CYB 115A CYBERSECURITY FUNDAMENTALS
This course provides a bird’s eye view of the evolving cyberspace ecosystem, the interoperability of physical and social networks, and methods and techniques in securing that ecosystem. Students will explore the ethical, legal, and technical aspects of cybercrime and methods of prevention, detection, response and recovery. The value of strong moral character, integrity, and trust as prized attributes of cybersecurity practitioners will be highlighted. Students will be introduced to essential cybersecurity topics including operating system models and mechanisms for mandatory and discretionary controls, data models, basic cryptography and its applications, security in computer networks and distributed systems, inspection and protection of information assets, detection of and reaction to threats to information assets, and examination of pre- and post-incident procedures, technical and managerial responses, an overview of the information security planning and staffing functions, data mining and data science, and policy and assurance issues. The advantages and inherent value of being prepared as a life-long learner with a
strong liberal-arts background will be emphasized with the opportunity for students to complete a service-learning project tailored to their academic/career goals. No prior computer programming experience is required. Basic competency in computer operation is required.CSC/CYB 230A NETWORKING AND DATA COMMUNICATIONS
This course expands upon the principles and current trends in computer networks as identified in Cybersecurity Fundamentals. Students will deepen their understanding of wide area networks (WANs), local area networks (LANs) and their architectures across which data travels and communicates. Subjects will include the open systems interconnection (OSI) model, transmissions control protocol / internet protocol (TCP/IP), open systems, topologies and internet connected devices. Through in-class projects, theoretical and practical approaches toward building and maintaining local area networks will be covered.CSC/CYB 235A SECURING WIRED AND WIRELESS NETWORKS
This course provides students who have a basic understanding of computer networking and data communications with the methods and techniques used to secure networks. Students will be required to design and build a secure local area network, incorporating all elements of the seven layers of the OSI Model. Students will learn the capabilities, limitations and vulnerabilities of a cyber network that can be dynamic yet strong against aggressive hackers and virus outbreaks. Also, the goal of this course is to provide students with both technical and theoretical approaches to the deployment, securing and defending of wireless networks. Topics will address network attacks, intrusion detection, malware, rogue wireless networks and wireless networking through the cloud. Students must already possess a basic knowledge of information security and networks. Team projects and presentations are required for completion.CYB 265A OPERATING SYSTEMS ADMINISTRATION
Learn how best to protect computers, the data they store, process, and transmit, and the users who use them, from a wide array of cybersecurity threats. This course will introduce students to operating systems administration within the context of cybersecurity. Students will learn how best to perform basic system administration operations with an emphasis on methods (e.g., managing applications, services, and network ports) to fortify the security of the computer’s operating system. The class will provide coverage of methods used in the Microsoft Windows® and Linux® operating systems.CYB 304A CRYPTOGRAPHY
Cryptography is a key component in securing data while it is stored, processed, and transmitted. Cryptography components are found in computer applications and also utilized to secure network communications. This course will introduce students to the principles of cryptography, cryptographic number theory, including hash functions, symmetric and asymmetric cryptography, and their common applications in network security and corresponding susceptibility to attacks/failures. Students will learn how best to compare, select, and apply cryptographic approaches to fortify cybersecurity. Other topics include cryptographic algorithms and programming.CYB 318A SOFTWARE AND APPLICATION SECURITY
Software security represents a key aspect in the field of cybersecurity. This course will ground students in the concepts of malware, malware analysis and preventive measures during software development that can mitigate malicious activity. Theoretical approaches to software security will be complemented by practical scenarios from which students can conduct future software design and investigations.CYB 328A COMPUTER NETWORK FORENSICS AND DIGITAL INVESTIGATIONS
This course studies the technology and practice of investigating the abuse of computing systems and digital devices. As criminal and adversarial activity becomes faster and less visible over networks, students must understand how to search for, and extract information from, cyberspace. This course will provide unparalleled insight into digital forensics methods and laws, complemented with practical lab work. This course also introduces students to the theory and practice of network traffic analysis and intrusion detection. Students will learn “traceback” techniques and information retrieval methods to identify different attacks. Topics covered will include network forensics, intrusion detection and response, case studies, and issues of cyber law and ethics. Students must have basic knowledge of networking, and operating systems. Team projects and presentations are required for completion.CYB 338A ETHICAL HACKING
This course will introduce students to ethical hacking and penetration testing methods, learning to think like a cyber-criminal and develop secure countermeasures. Students will learn the systematic approaches to planning, reconnaissance, vulnerability identification and exploitation methods used by hackers around the world to compromise the security of existing networks, systems, and applications. A variety of penetration-testing tools and techniques will be explored through hands-on activities. Identification of corresponding cybersecurity control recommendations will be highlighted.CYB 401A PREPARING FOR CYBER DISASTERS
This course will provide students a full picture of securing a firm from a cyberattack. Topics will include preparatory measures that continuously investigate network integrity, data security, and backup archives. Students will also develop Cyber Disaster Response Plans that consider the legal, economic, and physical requirements needed to recover from a cyberattack.CYB 438A INDEPENDENT CYBERSECURITY PROJECT OR INTERNSHIP
Students in the Cybersecurity program will have the option during one semester to conduct and present an independent cybersecurity project or intern part time with a cybersecurity employer in the business, government or nonprofit sectors. This course is designed to provide a culminating experience that avails students the opportunity to apply what they have learned to a contemporary cybersecurity project or internship experience that is framed by current cybersecurity industry trends and concerns. The course also helps students continue to improve skills critical to success in pursuit of their future academic and career aspirations. -
For the 2024- 2025 academic year, tuition is $850 per credit. There are no fees associated with this program.
-
ESTIMATED COSTS
(Please refer to Post- Bachelor’s Accelerated Cybersecurity Track website for details on actual costs.)
Cost of Attendance
- Direct charges – what you will pay to Assumption University
- Indirect charges – estimates of what you will pay during the academic year outside of Assumption University
2024-2025 & 2025-2026 Academic Year Direct Charges Tuition $850 per credit Indirect Charges Housing & Food $5,048 per term Books/Supplies $500 per term Personal Expenses $500 per term Transportation $500 per term FINANCING YOUR ASSUMPTION UNIVERSITY EDUCATION
As a post-baccalaureate student, you have a few options to finance your education:
- Federal Direct Student Loans
- Private Loans
- Scholarships
- Billing & Payment Plans
Federal Direct Student Loans
Given the various low-interest loan options available through the U.S. Department of Education, we encourage you, no matter your income level, to apply for federal financial aid by submitting a FAFSA (Free Application for Federal Student Aid)—it’s the only way to know what type of federal loan you’re qualified to receive. You can file your FAFSA at www.studentaid.gov. To be eligible for federal student financial aid, you must be:
- Accepted into a degree program.
- Enrolled in at least six credit hours per term.
- A U.S. citizen or eligible noncitizen – https://studentaid.gov/understand-aid/eligibility/requirements
Start date for program:
Spring 2025 2024-2025 FAFSA required.
Summer 2026 2025-2026 FAFSA required.
Fall 2026 2025-2026 FAFSA required.
Students accepted into Assumption’s Post- Bachelor’s Accelerated Cybersecurity Track have already obtained their first bachelor’s degree. As a second-degree student filling out the FAFSA, here are some details you will need to know:
- Federal School code: 002118 – Assumption University
- Grade level: Fifth year/other undergraduate.
- Degree type: Second bachelor’s degree
- Graduate/Professional program: No
- Assumption’s Post- Bachelor’s Accelerated Cybersecurity Track is not a graduate program so you will only be considered for undergraduate federal direct loans if you submit a FAFSA. If you borrowed federal direct loans for your first bachelor’s degree, these loan amounts will be counted towards your federal student loan undergraduate aggregate borrowing limit listed below.
For additional information on Federal Student Loans for Undergraduate Students, please visit, www.studentaid.gov.
The following chart shows the annual and aggregate limits for subsidized and unsubsidized loans.

If you are a new student at Assumption University and are offered a Federal Direct Student Loan, you will need to complete a Master Promissory Note (MPN) and Entrance Counseling at www.studentaid.gov before the funds can be used as a credit against your bill.
Private Loans
More times than not, federal student aid will not cover the total cost of attending our financing the Post- Bachelor’s Accelerated Cybersecurity Track program. Therefore, it is a good idea to research private lenders, such as banks or credit unions, and try to borrow from an institution with low-interest rates and good terms.
With private loans, you can choose a fixed interest rate (stays the same) or a variable interest rate (fluctuates). It is also a good idea to see what type of borrower protection a lender offers, such as flexible repayment plans or payment deferral.
Furthermore, because private loans are credit-based, it is important to know your credit score. If you have poor credit, you are likely to pay a higher interest rate than you would with a federal loan. You may even need a co-signer on your loan.
You can view some of the most popular loans taken by Assumption students and their families by going to www.elmselect.com and selecting Assumption University.
Scholarships
Assumption University does not offer any institutional scholarship or grant funding to students in the Post- Bachelor’s Accelerated Cybersecurity Track. However, we strongly recommend that you look into applying for outside scholarship funding to help reduce the cost of your education. If you do receive an outside scholarship, please be sure to report it to our office by completing the Outside Scholarship Reporting Form located on our website at s1auviv.wpengine.com/FAforms.
Please Note: Outside scholarship funds will not show as a credit on your bill until the funds are received by the Assumption University Student Accounts Office.
For additional information on billing and payment plan options, please visit Assumption’s Student Accounts Office – Billing and Payment Plans.
Contact Information: studentaccounts@assumption.edu or at (508) 767-7351.
CONTACT US
Please visit our website to see how you can contact us:
s1auviv.wpengine.com/ContactFA
-
Assumption University Cybersecurity program graduates will be able to:
- Apply knowledge of computing and information technologies and use software development and security analysis tools to produce effective designs and solutions for specific cybersecurity problems within a variety of computing platforms and employing an approved secure systems development process model;
- Identify, analyze, and synthesize scholarly and professional literature relating to the fields of cybersecurity, information security, or information assurance, to help solve specific problems and to stay abreast of the rapidly changing security context;
- Participate as an active and effective member of a project team engaged in achieving specific computer-based cybersecurity results or solutions;
- Communicate, both orally and in writing, and negotiate with colleagues and other stakeholders including employees, managers, and executives within and between organizations;
- Demonstrate sensitivity to and sound judgment on ethical issues as they arise in cybersecurity and will adhere to accepted norms of professional responsibility;
- Integrate their technical expertise with knowledge from other disciplines, such as computer science, data analytics, economics, management science, psychology and human factors, to arrive at practical cybersecurity solutions that are effective in real organizations; and
- Use appropriate tools to prevent, detect, respond, and recover from cyber-attacks.
-


Assumption University’s cybersecurity program has achieved “Program of Study” validation. This validation is awarded by the National Academic Excellence in Cybersecurity (NCAE-C) program – which is managed by the NSA – and it means the University’s cybersecurity curricula and its B.S. in Cybersecurity degree meets or exceeds NSA standards in articulating cybersecurity education. In addition, the liberal arts foundation of the program directly aligns with and supports the following NCAE-C program core values and guiding principles:
- The Ethical Behavior Core Value: The academic institution must encourage and support ethical behavior by students, faculty, administrators, and professional staff.
- The Share Core Value: The institution enables an environment in which students, faculty, administrators, professional staff, and practitioners can share, interact, and collaborate with others in the cybersecurity field.
- The Lead by Example Core Value: The institution demonstrates a commitment to address, engage, and respond to current and emerging cybersecurity issues in the classroom, the institution itself, and outside the institution.
-
 Professor Raymond T. Albert is Director of Cybersecurity Program and Professor of Practice at Assumption University and has formerly served as Director of the Maine Cyber Security Cluster (MCSC) at the University of Southern Maine (USM). Ray previously served as Chair of the Division of Natural and Behavioral Sciences at the University of Maine at Fort Kent (UMFK) during which time he orchestrated the effort to achieve program accreditation under the auspices of the International Assembly for Collegiate Business Education (IACBE). While at UMFK, he also successfully orchestrated and led a multi-campus initiative to attain National Security Agency (NSA)/Department of Homeland Security (DHS) recognition of the distributed University of Maine System (UMS) Center of Academic Excellence in Information Assurance and Cyber Defense Education. He now serves as a program reviewer for other institutions seeking recognition. Ray has also served the New England Association of Schools and Colleges (NEASC) Commission on Institutions of Higher Education (CIHE) as an on-site evaluator for higher education institutions in New England. In 2007, both chambers of the Maine State Legislature passed a legislative sentiment recognizing his work in higher education in the St. John Valley. The proclamation was sponsored, and later presented to Albert, by Fort Kent area Representative Troy Jackson and Senator John Martin. Ray’s industry experience includes serving NASA – Johnson Space Center as a Software Quality Assurance Engineer on its Space Station Freedom Project, Macro Development Corporation as a software developer, and QualityQuest, LLC as a CEO.
Professor Raymond T. Albert is Director of Cybersecurity Program and Professor of Practice at Assumption University and has formerly served as Director of the Maine Cyber Security Cluster (MCSC) at the University of Southern Maine (USM). Ray previously served as Chair of the Division of Natural and Behavioral Sciences at the University of Maine at Fort Kent (UMFK) during which time he orchestrated the effort to achieve program accreditation under the auspices of the International Assembly for Collegiate Business Education (IACBE). While at UMFK, he also successfully orchestrated and led a multi-campus initiative to attain National Security Agency (NSA)/Department of Homeland Security (DHS) recognition of the distributed University of Maine System (UMS) Center of Academic Excellence in Information Assurance and Cyber Defense Education. He now serves as a program reviewer for other institutions seeking recognition. Ray has also served the New England Association of Schools and Colleges (NEASC) Commission on Institutions of Higher Education (CIHE) as an on-site evaluator for higher education institutions in New England. In 2007, both chambers of the Maine State Legislature passed a legislative sentiment recognizing his work in higher education in the St. John Valley. The proclamation was sponsored, and later presented to Albert, by Fort Kent area Representative Troy Jackson and Senator John Martin. Ray’s industry experience includes serving NASA – Johnson Space Center as a Software Quality Assurance Engineer on its Space Station Freedom Project, Macro Development Corporation as a software developer, and QualityQuest, LLC as a CEO. -
I’ve never taken asynchronous online classes. What can I expect?
Asynchronous online classes provide wonderful flexibility for students to access course materials on the days and times that fit their schedule. Our faculty use a variety of teaching methods to help meet various learning needs of our students. You can expect to have reading assignments (textbooks, articles, or other materials), interactive materials (ATI modules, audio/visual case studies, or discussion board activities), recorded lectures, or projects you may complete with classmates. Some students may struggle in the transition from face-to-face learning in the traditional format to asynchronous online courses. Here are some important study tips to help make you a successful hybrid student:- Embrace independent learning: hold responsibility for the learning process
- Create goals that will help you organize your responsibilities and coursework
- Focus on becoming a proficient reader & communicator
- Set a schedule and stick to it!
- Learn basic computer skills and develop a general comfort level in cyberspace
- Prioritize deadlines
- Adhere to “netiquette”
If I’m learning online, how will I connect with my professors?
Faculty in the Post-Bachelor’s Accelerated Cybersecurity Track are passionate about maintaining a supportive, intellectual learning community through the virtual platform. You may have the opportunity to meet face-to-face on days you visit campus, or virtually through Zoom at other times during the week. We know that flexibility and accessibility are important factors when learning in a hybrid environment!
Faculty


Joshua Nixdorf
Cybersecurity 2024
“ The amount of time and effort put in by both the students and the staff for the success of the program has been nothing short of monumental. The Assumption Cybersecurity program has given me the tools necessary to make great advancements in the ever-changing modern world. Being able to work using various technologies on actual real-world problems not only helped to solidify my faith in the program, but also helps to promote student creativity on how to approach problems in a not-so cookie cutter world.”

Andrew Ellis
Cybersecurity 2023
Compliance Analyst at RTX
“ Assumption’s curriculum and cybersecurity program allowed me to hone my skills and become a more well-rounded individual. I am extremely grateful to be graduating from Assumption. The professors are very passionate about teaching and want all their students to achieve success. The variety of courses has helped me discover new interests and passions for subjects I may not have otherwise. The cybersecurity program has prepared me for the future in whichever area of the field I pursue. ”

Matthew McNaughton
Cybersecurity 2023
Cybersecurity & Technology Auditor with Liberty Mutual Insurance








 Professor Raymond T. Albert
Professor Raymond T. Albert